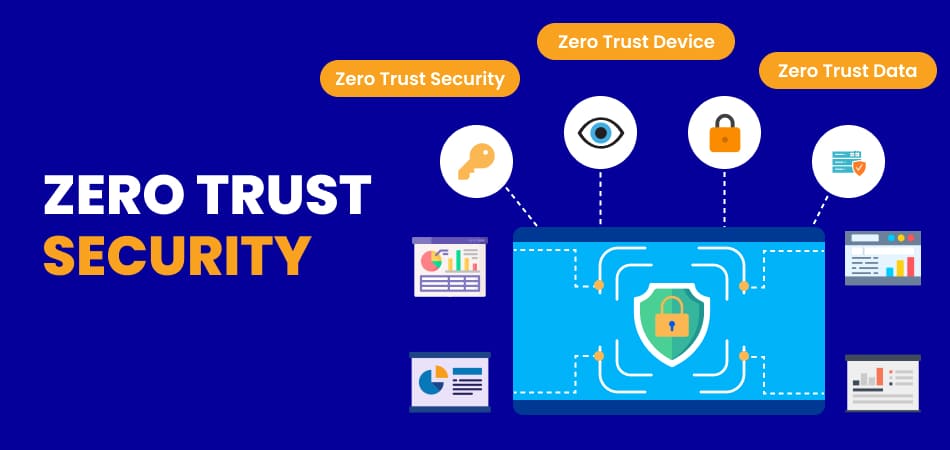
In an era where cyber threats are becoming increasingly sophisticated, traditional security models are no longer sufficient to protect sensitive data and maintain the integrity of digital systems. This has led to the rise of Zero Trust Security Models, a revolutionary approach that promises to address these emerging cyber threats more effectively. This blog delves into how Zero Trust Security Models work, their benefits, and how they address the evolving landscape of cyber threats.
Introduction to Zero Trust Security Models
The Zero Trust Security Model operates on a straightforward principle: “Never trust, always verify.” Unlike traditional security models, which assume that everything within an organization’s network is inherently trustworthy, Zero Trust recognizes the potential for threats from both internal and external sources. As a result, it mandates continuous validation at every stage of digital interaction, irrespective of the user’s location within the network.
The Evolution of Cyber Threats
- Increasingly Sophisticated Cyber AttacksMore sophisticated methods are being used by cybercriminals to compromise networks. From ransomware to phishing and zero-day exploits, the threat landscape is constantly evolving. Traditional security measures like firewalls and antivirus software are no longer sufficient to counter these threats.
- The Rise of Insider Threats
Insider threats, whether malicious or accidental, have become a significant concern for organizations. Employees with access to sensitive information can inadvertently or deliberately cause substantial damage, making it imperative to continuously monitor and verify user activities. - The Proliferation of IoT DevicesThe Internet of Things (IoT) has introduced millions of connected devices, each representing a potential entry point for cyber attackers. Securing these devices with traditional perimeter-based security models is impractical and often ineffective.
Core Principles of Zero Trust Security
| Principle | Description |
| Least Privilege Access | Ensures users only have the minimum access necessary to perform their tasks. |
| Continuous Monitoring | Continuous validation of user activities, device integrity, and network activity to detect threats. |
| Micro-Segmentation | Dividing the network into more manageable, separate sections to restrict attackers’ ability to move laterally. |
| Multi-Factor Authentication (MFA) | Requires users to provide multiple forms of verification to access the network. |
Addressing Emerging Cyber Threats with Zero Trust
- Mitigating Ransomware AttacksRansomware attacks have become increasingly prevalent and damaging. Zero Trust Security Models mitigate these attacks by limiting access to critical systems and data. Even if a user account is compromised, the attacker’s ability to spread ransomware within the network is significantly reduced.
- Combating Phishing AttacksPhishing remains one of the most prevalent tactics for cybercriminals to obtain access to sensitive information. Zero Trust addresses this by implementing MFA and continuous monitoring, which helps detect and block phishing attempts before they can cause harm.
- Protecting Against Zero-Day ExploitsZero-day exploits take advantage of unknown vulnerabilities in software and hardware. Zero Trust’s continuous monitoring and validation can identify unusual behavior patterns that may indicate an exploit, allowing organizations to respond swiftly and minimize damage.
- Securing IoT DevicesIoT devices often have limited security features, making them prime targets for cyber attackers. Zero Trust enhances IoT security through micro-segmentation and continuous monitoring, ensuring that compromised devices cannot be used to access other parts of the network.
Implementing Zero Trust Security Models
- Assessing Current Security PostureThe first step in implementing a Zero Trust Security Model is to assess the organization’s current security posture. This involves identifying critical assets, existing vulnerabilities, and potential threats.
- Defining Access PoliciesOrganizations must define clear access policies based on the principle of least privilege. This involves determining who needs access to what resources and under what conditions.
- Implementing Multi-Factor AuthenticationMFA is a critical component of Zero Trust. Implementing MFA across all access points ensures that even if one authentication factor is compromised, unauthorized access is still prevented.
- Deploying Advanced Monitoring ToolsContinuous monitoring is essential for Zero Trust. Organizations must deploy advanced monitoring tools that can analyze user behavior, device integrity, and network activity in real-time.
- Adopting Micro-Segmentation
Attackers’ ability to move laterally throughout the network is restricted by micro-segmentation. Implementing micro-segmentation involves dividing the network into smaller segments and enforcing strict access controls for each segment. - Educating EmployeesEmployees play a crucial role in the success of Zero Trust. Organizations must educate employees about the importance of security best practices, recognizing phishing attempts, and reporting suspicious activities.
Benefits of Zero Trust Security Models
| Benefit | Description |
| Enhanced Security Posture | Continuous validation enhances security against external and internal threats. |
| Improved Compliance | Helps meet regulatory compliance requirements with strict access controls and monitoring. |
| Reduced Attack Surface | Micro-segmentation and least privilege access reduce the attack surface, limiting potential damage. |
| Faster Threat Detection | Real-time analysis and monitoring enable quicker detection and response to threats. |
Case Studies: Successful Zero Trust Implementations
- Google’s BeyondCorpThe BeyondCorp program by Google is a shining example of a Zero Trust deployment done right. By shifting security controls from the network perimeter to individual users and devices, Google has enhanced its security posture and improved user productivity.
- Microsoft’s Zero Trust ApproachMicrosoft has adopted a Zero Trust approach across its organization, implementing MFA, continuous monitoring, and micro-segmentation. This has helped Microsoft protect sensitive data, detect threats more quickly, and improve compliance with regulatory requirements.
Challenges in Adopting Zero Trust Security Models
- Complexity of ImplementationA Zero Trust Security Model’s implementation might be difficult and resource-intensive. Organizations must carefully plan and execute each step to ensure a successful transition.
- Balancing Security and UsabilityIt might be difficult to strike the correct balance between security and usability. Organizations must ensure that security measures do not hinder user productivity or create unnecessary friction.
- Integration with Legacy SystemsIntegrating Zero Trust with legacy systems can be difficult. Organizations may need to upgrade or replace outdated systems to fully implement Zero Trust.
Future Trends in Zero Trust Security
| Trend | Description |
| AI and Machine Learning | Enhances threat detection and response by analyzing vast amounts of data and identifying patterns. |
| Expansion to Cloud Environments | Zero Trust becomes crucial for securing cloud environments as organizations migrate to the cloud. |
| User Behavior Analytics | Analyzes user behavior in real-time to detect anomalies and respond to threats more effectively. |
Conclusion
The Zero Trust Security Model has transformed the approach organizations take toward cybersecurity. By requiring continuous validation of every user and device, enforcing least privilege access, and utilizing advanced monitoring tools, Zero Trust offers a robust defense against modern cyber threats that surpasses traditional security measures. With cyber threats evolving rapidly, adopting a Zero Trust model is becoming essential for safeguarding sensitive data and preserving the integrity of digital systems.
In summary, although implementing Zero Trust can pose challenges, the advantages significantly outweigh the difficulties. By strengthening security posture, improving compliance, reducing the attack surface, and enabling faster threat detection and response, the Zero Trust Security Model is critical for addressing today’s dynamic cybersecurity landscape.